Change your password NOW! Hackers steal 184 million accounts from Facebook, Amazon, Netflix, Microsoft, more

Hackers were compiling a devastating database of 184,162,718 unique logins and passwords before it was discovered by a security researcher
|GBN | SORA

All products and promotions are independently selected by our experts. To help us provide free impartial advice, we will earn an affiliate commission if you buy something. Click here to learn more
Security researcher stumbles across "cybercriminal's dream"
Don't Miss
Most Read
Latest
Do you have an account with Facebook, Instagram, Netflix, Microsoft, or Amazon? You should take action now.
That's because personal information from 184 million accounts has leaked in a colossal data breach. The database includes usernames, passwords, email addresses, and more.
This terrifying treasure trove was described as a "cybercriminal's dream working list," by security researcher Jeremiah Fowler, who unearthed the devastating breach.
The newly-discovered 47 GB database represents an unprecedented security risk, containing 184,162,718 unique logins and passwords. Jeremiah Fowler analysed a small sample of 10,000 records and discovered details for the following services:
- Roblox
- Discord
- Microsoft
- Netflix
- PayPal
- Apple
- Amazon
- Nintendo
- Snapchat
- Spotify
- WordPress
- Yahoo

Jeremiah Fowler shared a screenshot of the 47GB database, showing how the stolen login details were sorted. The treasure trove of leaked credentials has now been hidden from public view
|JEREMIAH FOWLER
In the same sample, Jeremiah Fowler discovered 220 email addresses with .gov domains, linking them to more than 29 countries including the US, UK, Australia, Canada, China, India, Israel, and Saudi Arabia. These accounts could pose serious national security threats if exploited by cybercriminals.
Cybersecurity firm Malwarebytes said "the exposure of such a massive dataset should serve as a wake-up call." The brand has outlined several useful tips to secure your personal information, which we've included at the bottom of this article.
Switch to 1Password for FREE
The award-winning 1Password is designed to generate and store unguessable passwords, passkeys, credit card numbers, national insurance numbers, and much more. This encrypted vault is available across all of your favourite devices, including iPhone and Android, Windows and Mac computers, iPad and other tablets. Its built-in WatchTower feature evaluates password strength and warns about data breaches that impact you. 1Password is currently free to test for 14 days with no obligation to subscribe
Security expert Jeremiah Fowler stumbled across the vast database of stolen information earlier this month, while searching for vulnerabilities in major computer networks.
"This is probably one of the weirdest ones I've found in many years," he told WIRED. “As far as the risk factor here, this is way bigger than most of the stuff I find, because this is direct access into individual accounts. This is a cybercriminal’s dream working list.”
When Fowler discovered the database, it was publicly accessible, unencrypted, and not password-protected, meaning anyone could have accessed the sensitive information. The data breach didn't just include usernames and passwords — although there were plenty of those — but also authorisation URLs for various accounts, creating multiple pathways for potential exploitation of your personal data.
The breach likely resulted from infostealer malware rather than direct vulnerabilities in the platforms themselves, meaning your credentials were probably stolen from your own devices.
This malicious software is "designed specifically to harvest sensitive information from an infected system," according to Fowler, and silently extracts credentials stored in your web browsers, email clients, messaging apps, and even crypto wallets.
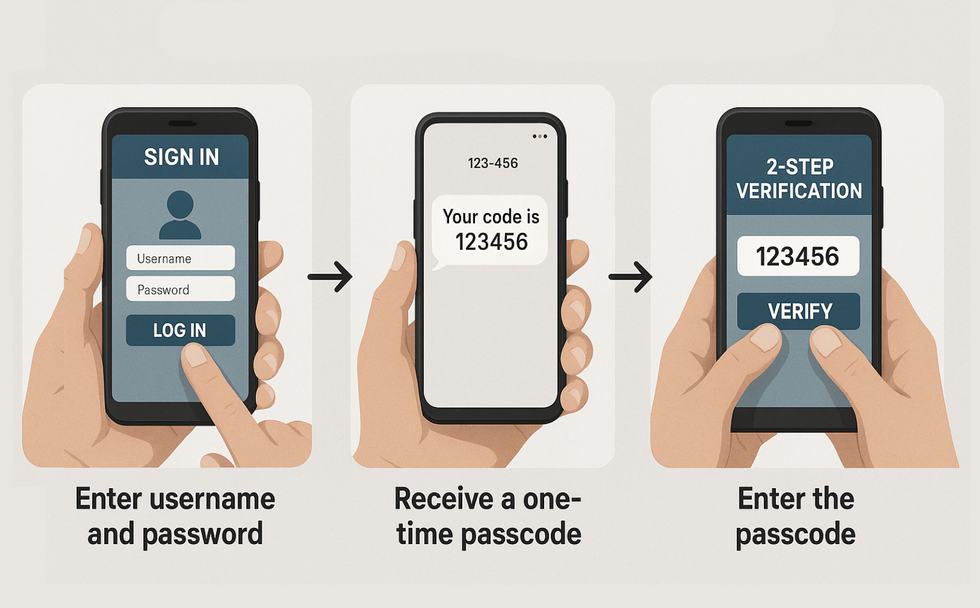
Two-Factor Authentication, sometimes stylised as 2FA, blocks anyone with your username (or email address) and password from logging into your account ...since they'll also need a one-time code sent to an inbox or mobile number
|GB NEWS
These malware variants often arrive through phishing emails, malicious websites, or bundled with cracked software that you might unknowingly download.
A Snapchat representative confirmed to Mashable that they have not found any evidence of a data breach or vulnerability on their platform, supporting the theory that your information was harvested directly from infected devices rather than company servers.
The exposure of your credentials creates multiple pathways for cybercriminals to exploit your digital life. Security experts warn that hackers could use your stolen usernames and passwords to commit identity theft, make unauthorised transactions, or engage in fraud using your personal information.
The breach also enables credential stuffing attacks, where criminals use your reused login details stolen from one service to access your other accounts.
"If a criminal can tie all these different types of stolen information to one person, like the operator of an infostealer would, it would be easy to use those details for identity theft," according to cybersecurity analysis.
Your personal details could be at risk if you use any of the affected services.
Security experts urgently recommend that anyone who uses one of the affected platforms change passwords immediately and enable two-factor authentication.
The latter adds an extra layer of security by sending a secure one-off code to your phone number or email, ensuring that username and password alone is not enough to login. You should use unique, complex passwords for every service and avoid reusing them across multiple accounts.
LATEST DEVELOPMENTS
- Your Android phone is about to unlock 'biggest update in years'
- Best VPN deals
- Switch from BT, Sky or EE broadband and unlock FREE internet bills
- All Sky Q viewers awarded FREE gift after nationwide TV outage
- Best Sky Stream deals
- Upgrade to Google's latest Android phone for under £15
Cybersecurity professionals also advise you to monitor your accounts for suspicious activity, including watching over your emails, banking apps, and social media accounts for changes that you did not make yourself.
"Many people unknowingly treat their email accounts like free cloud storage and keep years' worth of sensitive documents, such as tax forms, medical records, contracts, and passwords without considering how sensitive they are," Fowler warned.
The database was hosted by World Host Group, a web hosting and domain name provider founded in 2019 that operates over 20 brands globally. Once Fowler confirmed that your exposed information was genuine, he reported the breach to World Host Group, which promptly shut down access to the database.
Seb de Lemos, CEO of World Host Group, told WIRED: "It appears a fraudulent user signed up and uploaded illegal content to their server."
The company has since cooperated with the investigation, with de Lemos adding that "our legal team is reviewing any information we have that might be relevant for law enforcement."
The database has now been removed from public view, though it remains unclear how long your sensitive information was accessible to potential cybercriminals before Jeremiah Fowler's discovery.
Get 50% off subscription to NordPass password manager
NordPass is a secure password manager that works across your favourite devices, including iPhone and Android, Windows and Mac computers, iPad and other tablets ...it will evaluate your password strength, autofill login details for you, and warn about any data breaches on the Dark Web that impact you.
It's a one-stop-shop to improve your online security and fightback against hackers from the team behind the award-winning NordVPN
Cybersecurity firm Malwarebytes has shared several tips to protect yourself:
- Change your passwords regularly, and don’t reuse them across multiple accounts. Use unique, complex passwords for every service.
- Enable two-factor authentication (2FA) wherever possible. This makes it harder for criminals to take over your account.
- Regularly audit and clean your email inbox of sensitive documents and old passwords. Jeremiah pointed out that “people unknowingly treat their email accounts like free cloud storage and keep years’ worth of sensitive documents, such as tax forms, medical records, contracts, and passwords without considering how sensitive they are.”
- Use an up-to-date and active anti-malware solution that can detect and remove infostealer malware.
- Be careful about what you download and educate yourself on recognising phishing emails, as these remain the most common infection vectors.
Given the scale and sophistication of infostealer operations, it’s not enough to wait for breach notifications to find out whether your credentials have been compromised. That’s why proactive monitoring is essential.










